External Identity Providers Login Options
Follow the detailed instructions for providing Microsoft or Google OAuth login options to your CommPeak Dialer or Cloud PBX users and for signing in with SSO SAML.
In addition to the username/password sign-in, several other login options are available in CommPeak Dialer and Cloud PBX. You can choose the best methods for meeting your needs. All options provide secure ways for verifying the user's identity.
- Login with GoogleOAuth
- Login with MicrosoftOAuth
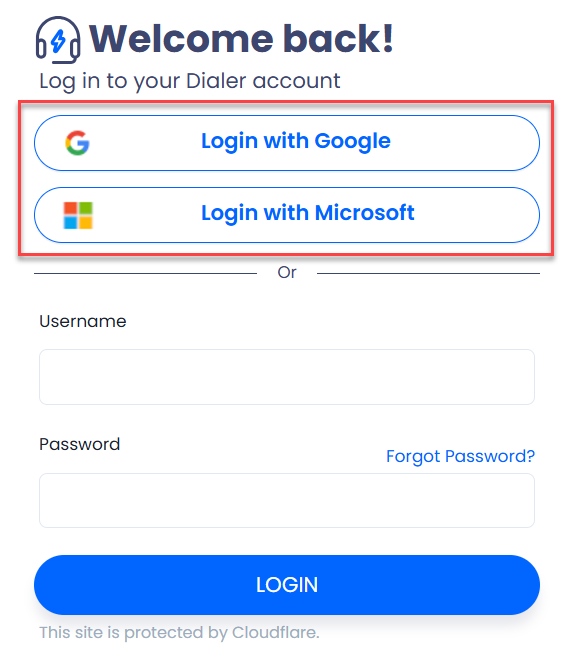
Login page with Google and Microsoft sign-in options highlighted
Both options above follow the OAuth 2.0 standard for secure authorization, enabling delegated access by issuing access tokens to third-party services without exposing user credentials. However, OAuth is solely for authorization — not authentication.
The OpenID Connect (OIDC) authentication layer is built on top of OAuth 2.0. Identity providers use OIDC so users can first sign in with their Identity Provider (IdP) and then access applications without having to log in and share credentials.
OAuth lacks encryption and relies on secure socket layer and transport layer security protocols (SSL/TLS), making it generally not a good choice for securing an enterprise with hundreds or thousands of employees.
- Login withSSO SAML only
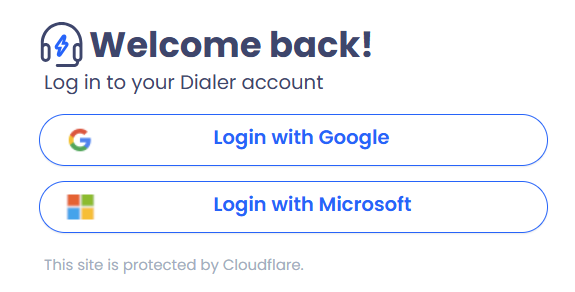
The login page with SSO sign-in only will not show the username credentials option
The CommPeak Dialer and Cloud PBX, supports Single Sign-On (SSO)-only mode, allowing users to log in without entering a username or password. For details on enabling SSO-only login, click here.
IMPORTANTEnsure SSO is working properly before enabling it as the sole login method. If SSO fails, the user may be locked out and need to contact support for assistance.
Undestanding SAML benefitsManaging passwords for applications used by hundreds or even thousands of employees can be extremely challenging. Security Assertion Markup Language (SAML) offers enterprises a single sign-on protocol.
SAML is a protocol that lets an IdP transmit a user's credentials to a service provider to both authenticate and authorize that user to access a service. SAML simplifies password management and enables SSO. It is helpful for enterprises because employees have access to more applications to carry out their jobs.
When a user requests access to the Dialer or Cloud PBX, it redirects the user to an IdP for authentication, which could be a service like GSuite or Okta. The IdP then verifies the user's identity, typically through methods like passwords or biometrics, and generates a SAML assertion response containing the user's authenticated identity. This SAML assertion response is sent back to the Dialer or Cloud PBX, which grants the user access based on the identity information provided in the response.
How to Turn On Google OAuth
To turn on the login with Google OAuth for your users:
-
Go to Settings > General Settings.
-
Scroll down to the Login Configuration section.
-
Toggle the slider to the right to enable the relevant option.
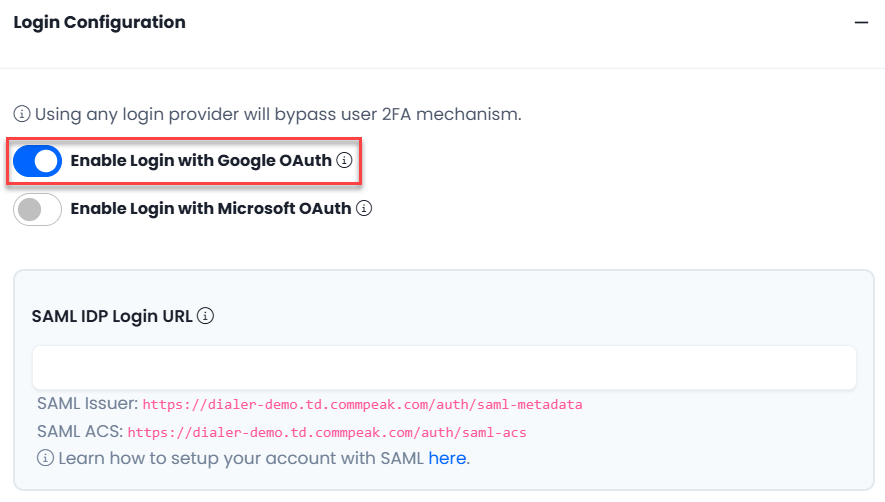
Login Configuration with Google OAuth option highlighted
NOTEPlease take into account the following information:
- This login option is available to all users with a Google email account.
- When a user logs in with Google and authorizes their Google email, the Dialer or Cloud PBX system searches for this email address in its database. The login is then associated with the first user account that matches the authorized Google email.
- If the system contains the same email address for more than one user, the login will be assigned to the first active user with that email.
- Sign-in from a standalone CommPeak Softphone doesn't support the Google login.
- This login feature bypasses both the login with email one-time code and two-factor authentication processes.
How to Turn On Microsoft OAuth
To turn on the login with Microsoft OAuth for your users:
-
Go to Settings > General Settings.
-
Scroll down to the Login Configuration section.
-
Toggle the slider to the right to enable the relevant option.
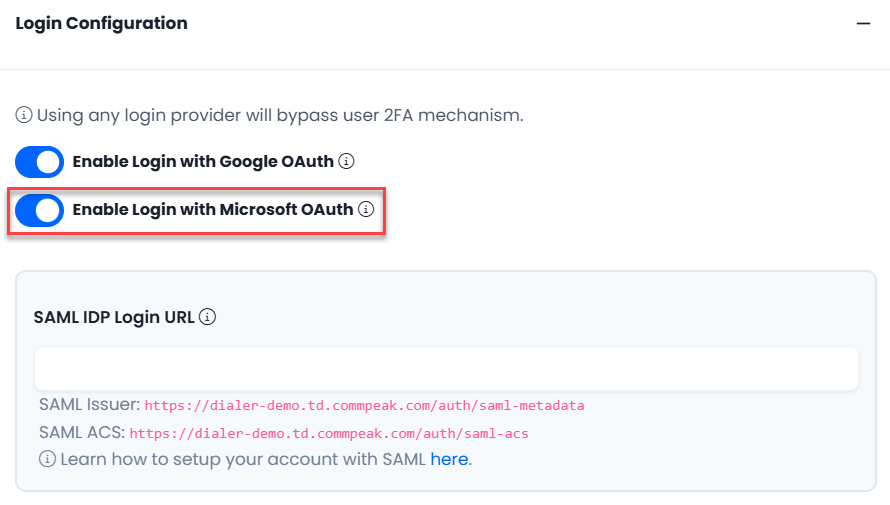
Login Configuration with Microsoft OAuth option highlighted
NOTEPlease take into account the following information.
- This login is available to any user utilizing Microsoft or Azure Email services, including Microsoft 365, and Live accounts.
- When a user logs in with Microsoft after authorizing their Microsoft email, the system searches for this email in the Dialer or Cloud PBX. The login is then assigned to the first user associated with the authorized Microsoft email.
- If the system contains the same email address for more than one user, the login will be assigned to the first active user with that email.
- This login option bypasses both the login with email one-time code and two-factor authentication processes.
How to Integrate with a SAML Provider
To integrate:
-
Go to Settings > General Settings.
-
Scroll down to the Login Configuration section.
-
Enable the account login with SSO SAML by inserting SAML Login URL, which must be obtained from your IdP. The Issuer URL and ACS URL are shown below the login URL.
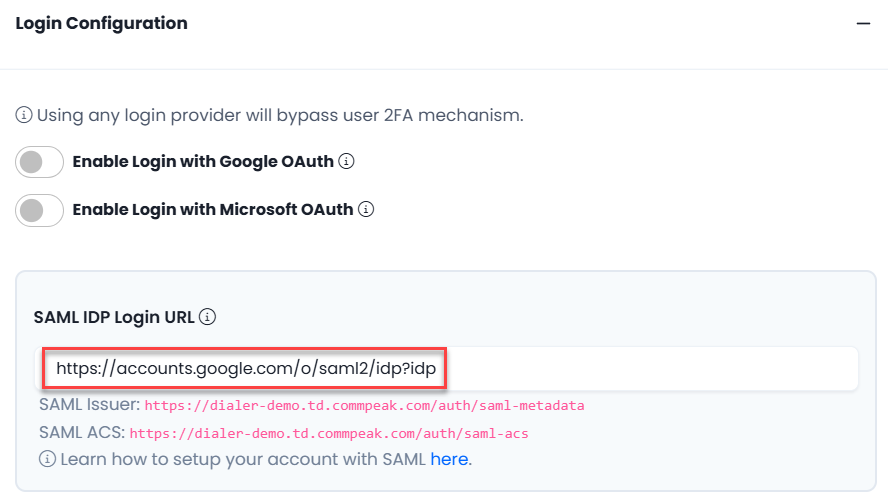
Login Configuration with SAML URL highlighted
NOTEPlease take into account the following information:
- SAML login lets you easily manage which users within your organization can access the Dialer or Cloud PBX. Users do not need to enter passwords; they simply click Login via SSO and authenticate through the customer's SAML IdP.
- Sign-in from the standalone CommPeak Softphone doesn't support the Login with SSO option.
- The system processes the email authorized by the customer’s SAML provider and logs in with the same active user email in the system. Deleted or inactive users cannot log in using SAML.
- This login option bypasses both the login with email one-time code and two-factor authentication processes.
SAML Setting Examples
Okta
Please visit Okta help instructions.
-
Create an integration.
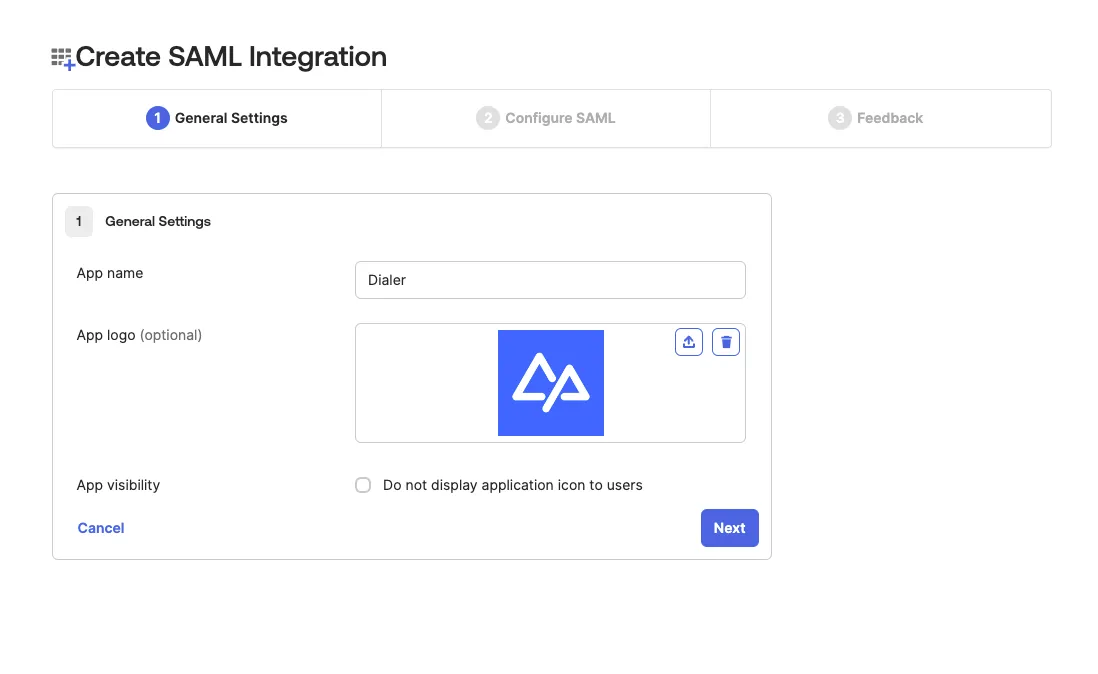
Create SAML Integration page - step 1
-
Insert the Dialer or Cloud PBX account access URL and issuer URL.
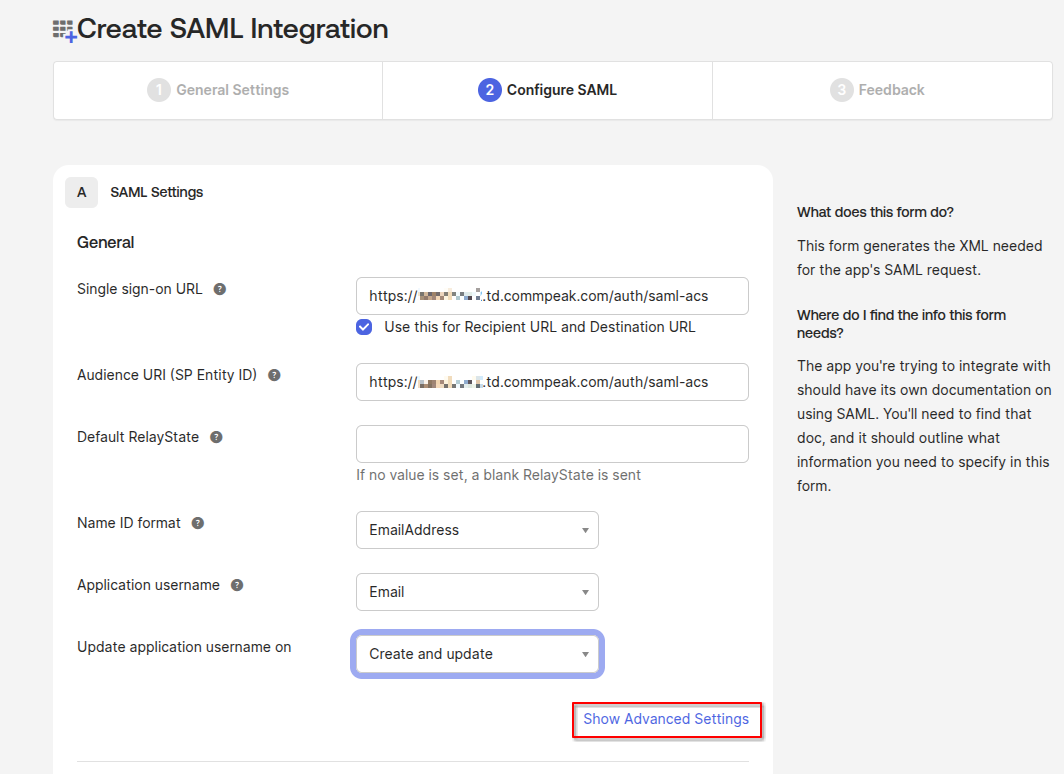
Create SAML Integration page - step 2
- Advanced settings.
Make sure to set "response", "Assertion Signiture" to Unsigned and "Assertion Encryption" to "Unencrypted".
SAML Issuer ID is your issues URL from your Dialer.
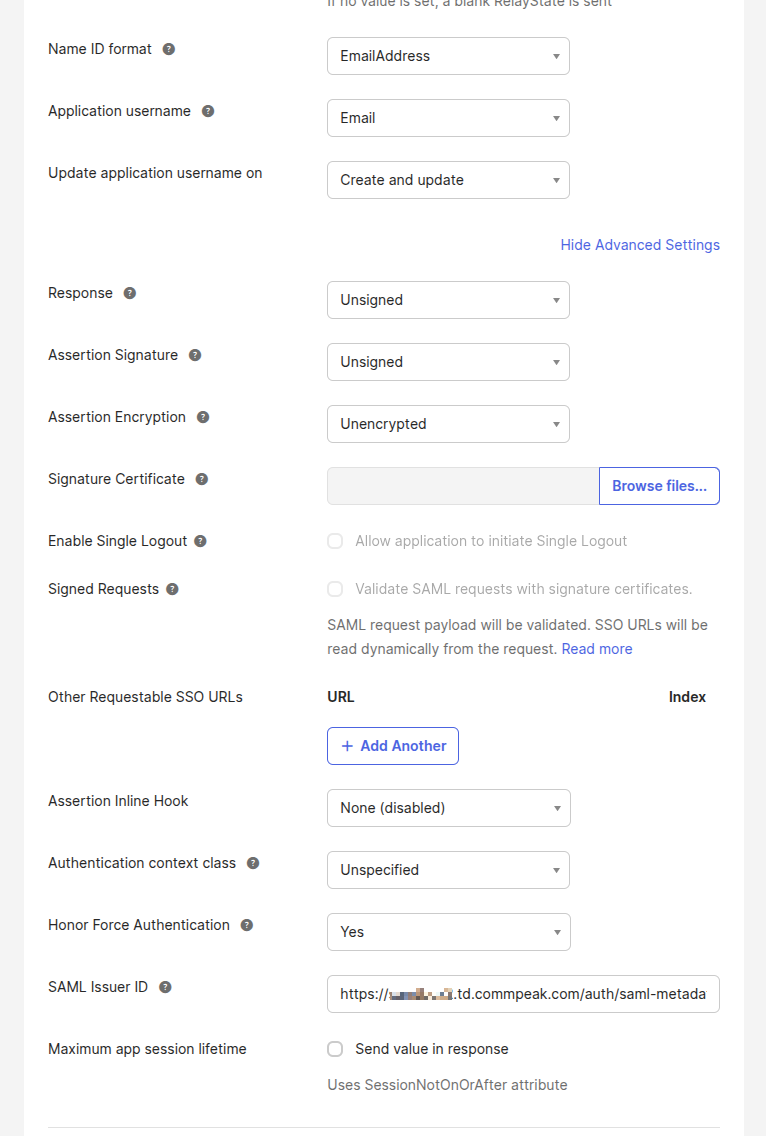
Advanced settings
-
Attributes setup:
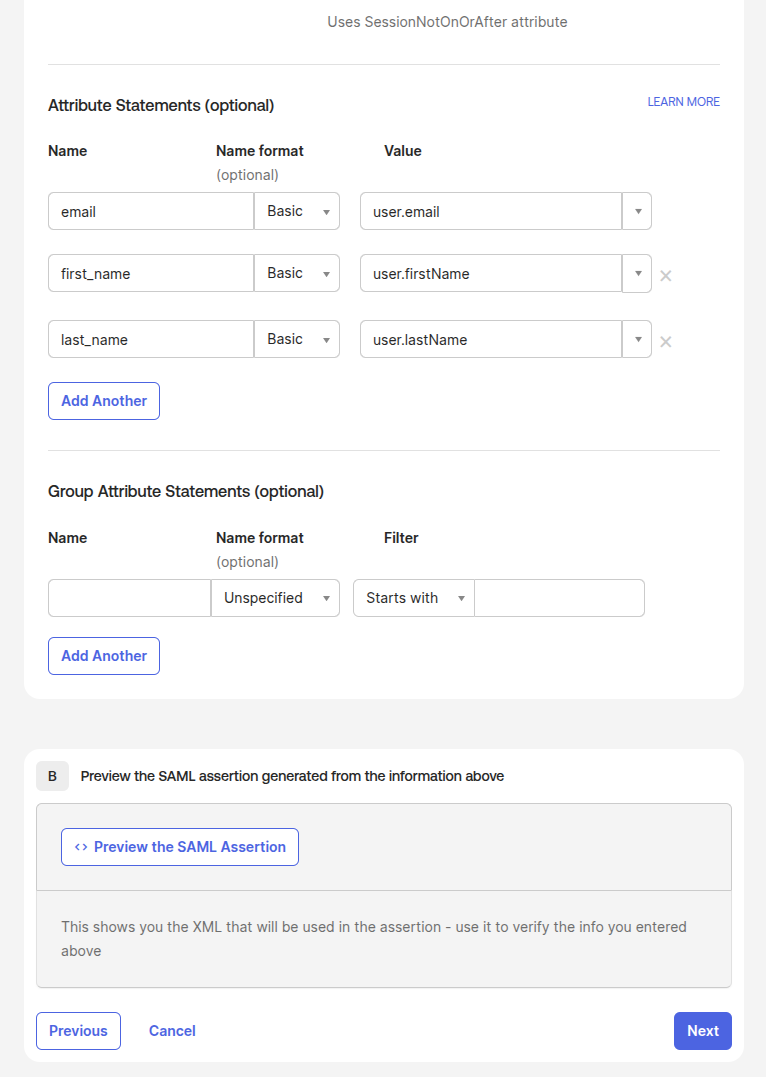
Advenced Settings
- Now, you can assign users in your organization to sign in via the Dialer or Cloud PBX SAML login.
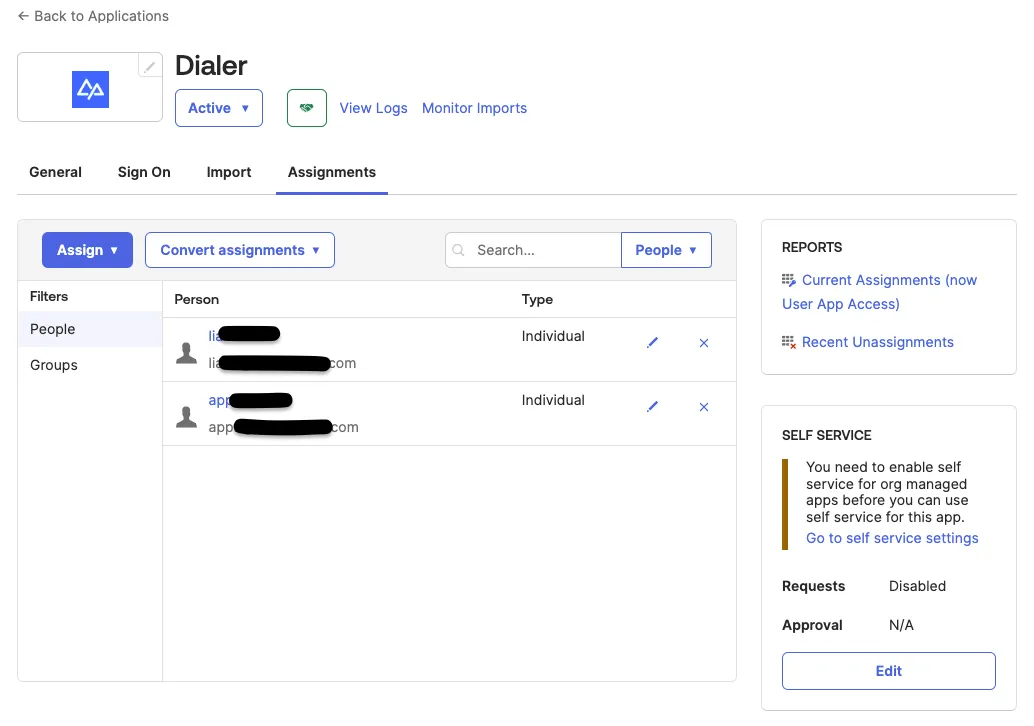
Assigning users action
-
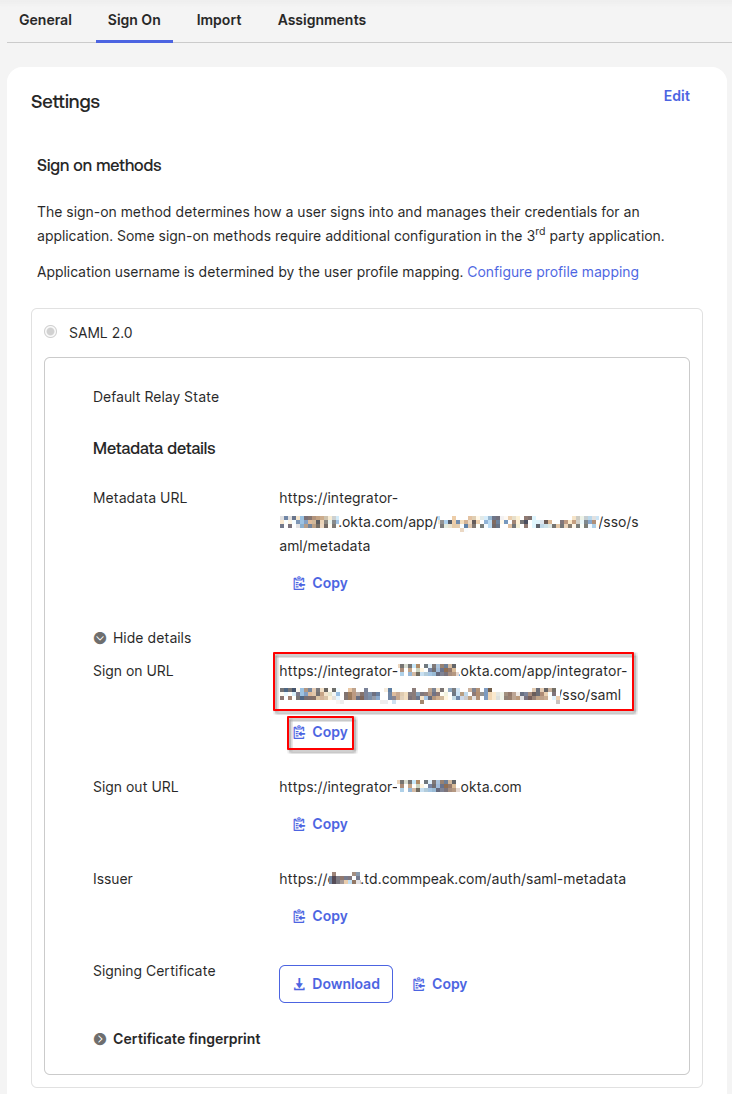
Go to Sign on tab, use the Sign On URL inside your Dialer setup SAML settings.
Google
Please visit Google help instructions.
-
Click Add custom SAML app.
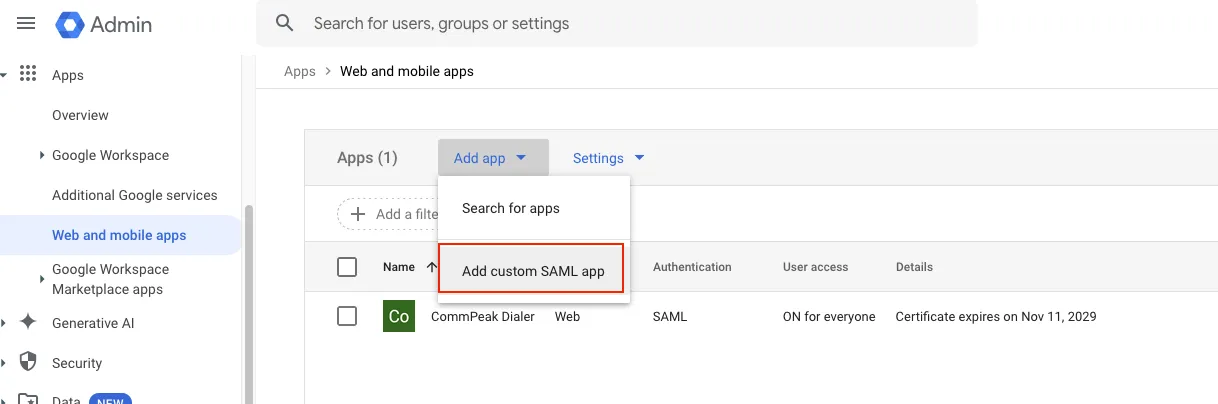
Apps with the Add custom SAML app option highlighted
-
Enter CommPeak Dialer, then click CONTINUE.
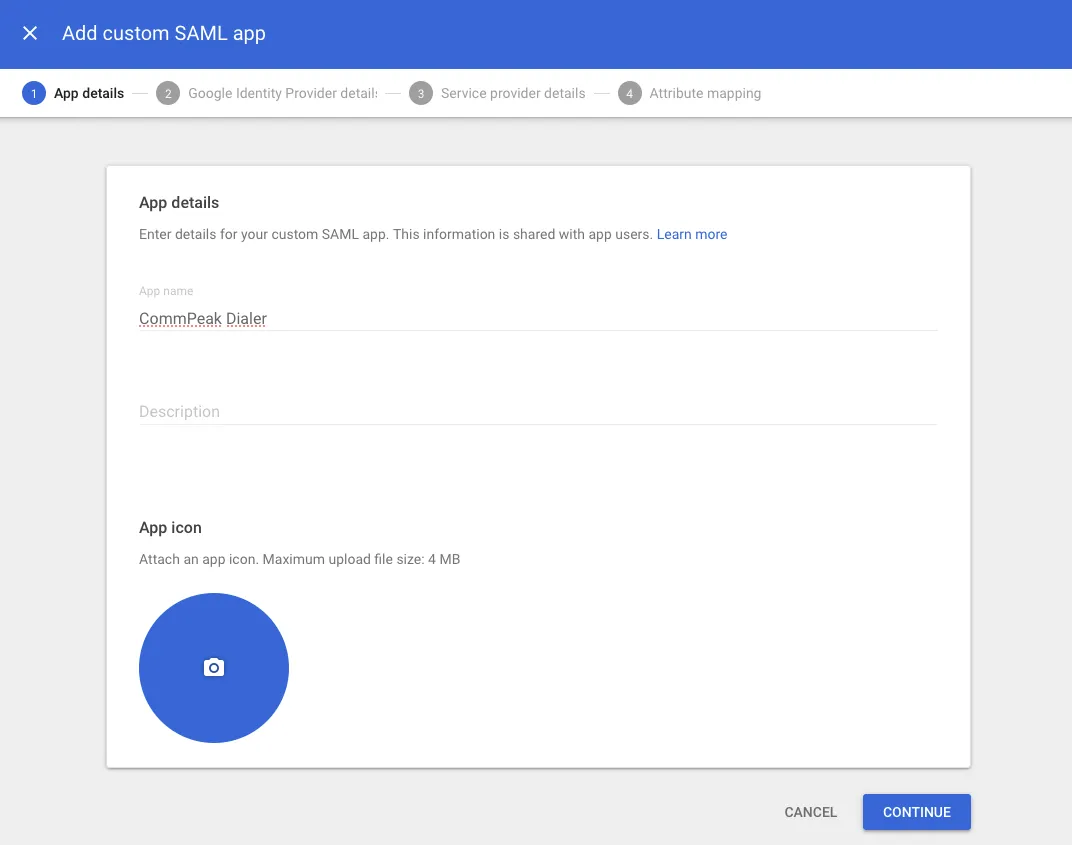
App Details form
-
Copy the SSO URL to the Dialer SAML IDP Login URL.
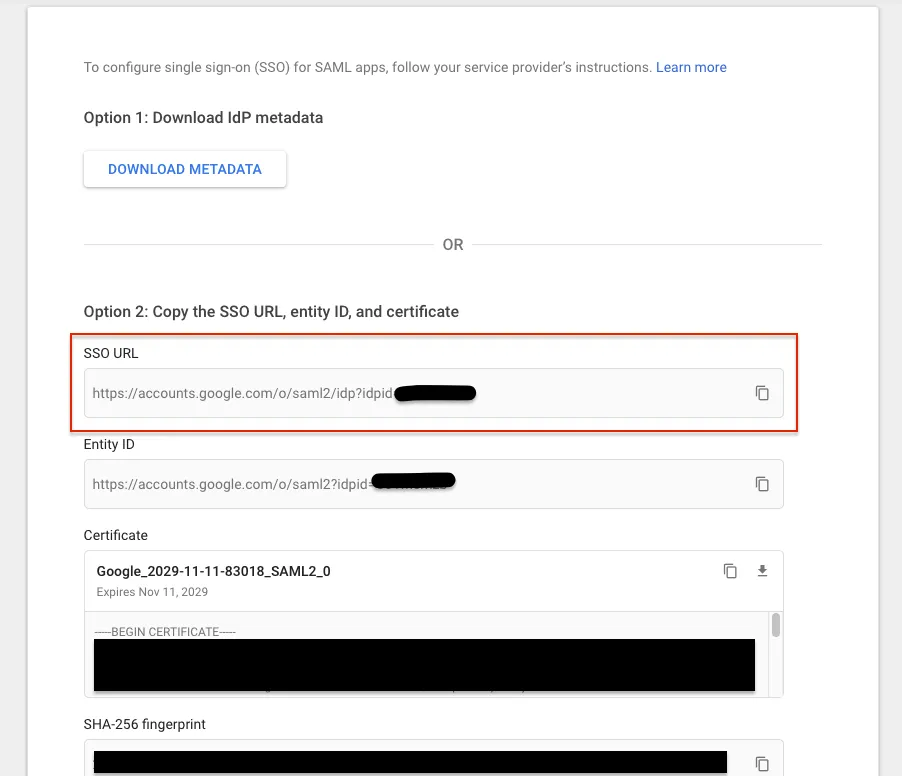
Configuration with SSO URL
-
Insert the Dialer issuer URL and ACS URL here.
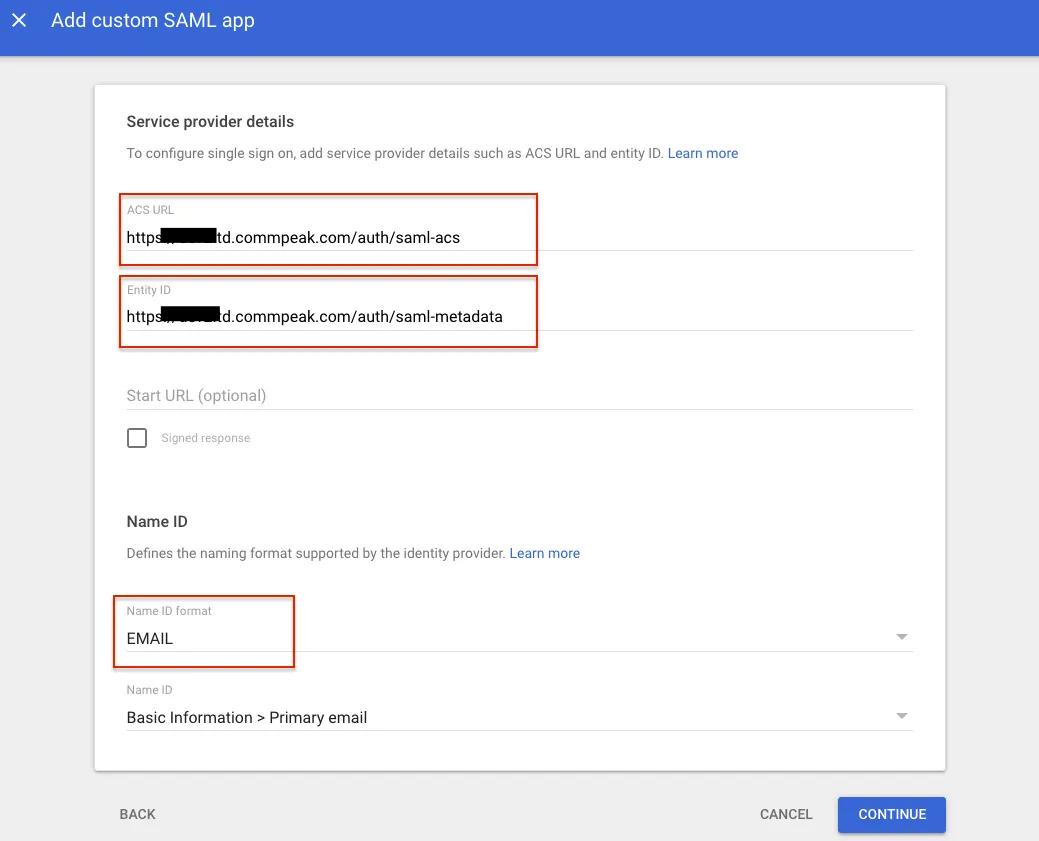
Adding custom SAML
-
After the setup is complete, you can test the login. Click TEST SAML LOGIN and proceed.
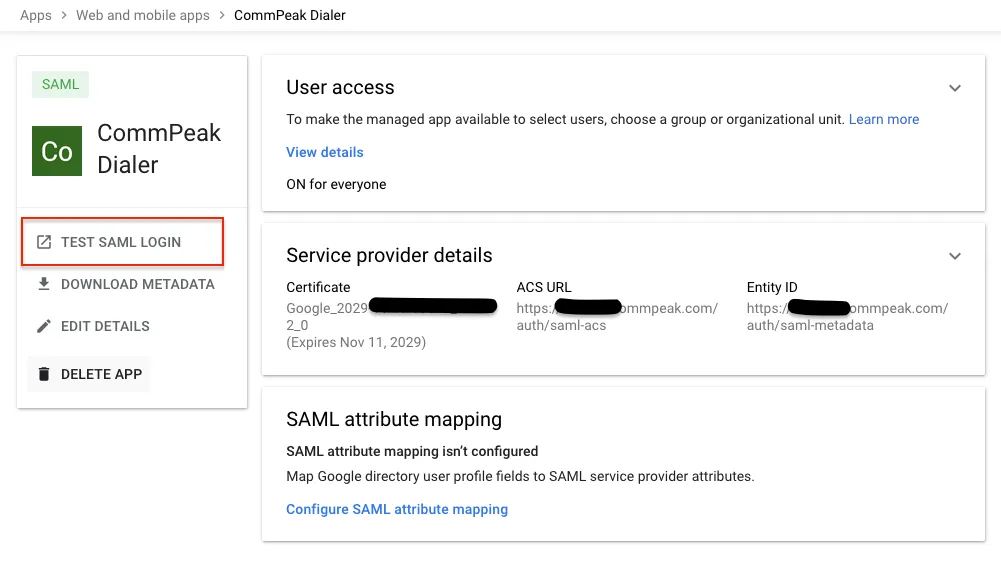
Testing the SAML login configuration
Microsoft Azure
-
In portal.azure.com find "Enterprise Applications"
-
Click on "New application" in the top bar
-
Search for “Microsoft Entra SAML Toolkit”, click on it, and install it by pressing the “Create” button in the right sidebar.
-
In the left pane, find "Properties" under "Manage", and set "Assignment Required" to "No". (This step might not be required, but assignment to groups and users must be defined instead)
-
Go to “Single sign-on” in the left pane under "Manage" and select "SAML"
-
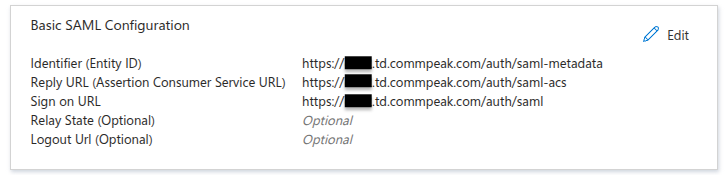
In "Basic SAML Configuration" define the following (replace dialer domain with the correct one):
-
Identifier (Entity ID):
<https://{account_name}.td.commpeak.com/auth/saml-metadata> -
Reply URL (Assertion Consumer Service URL):
<https://{account_name}.td.commpeak.com/auth/saml-acs> -
Sign on URL:
<https://{account_name}.td.commpeak.com/auth/saml>
-
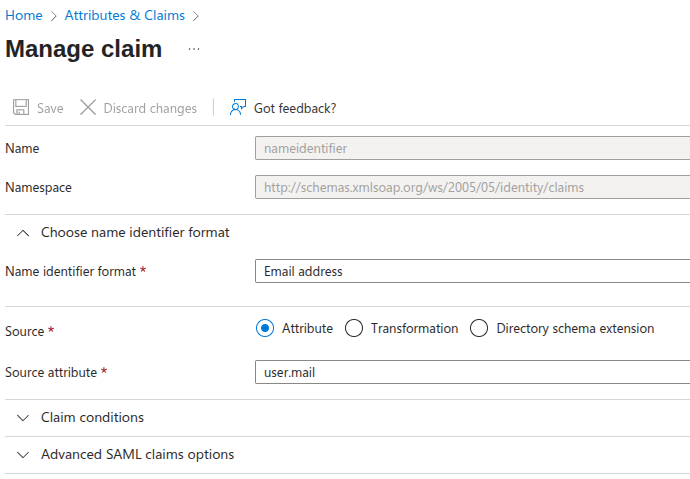
- Edit "Attributes & Claims" and verify "Required claim" configuration to have:
- Name identifier format - Email address
- Source attribute - user.mail
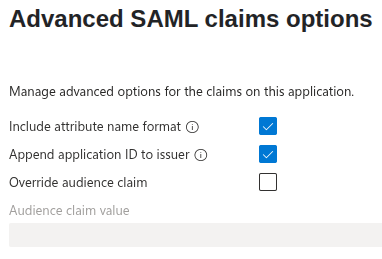
- Edit “Advanced SAML claims options” under “Advanced settings” and check the following checkboxes:
- Include attribute name format
- Append application ID to issuer
-
From “Set up Microsoft Entra SAML Toolkit” copy “Login URL” and place it in Tenant Settigns in Dialer as SAML Login URL
-
Your SAML Login LDP URL on dialer should looks like
https://login.microsoftonline.com/{azure_app_id}/saml2For more info, please visit Microsoft Azure help instructions page.
Updated about 1 month ago